A proxy botnet called ‘Socks5Systemz’ has been infecting computers worldwide via the ‘PrivateLoader’ and ‘Amadey’ malware loaders, currently counting 10,000 infected devices. The malware infects computers and turns them into traffic-forwarding proxies for malicious, illegal, or anonymous traffic. It sells this service to subscribers who pay between $1 and $140 per day in crypto to access it.
Access to Socks5Systemz proxying services is sold in two subscription tiers, namely ‘Standard’ and ‘VIP,’ for which customers pay via the anonymous (no KYC) payment gateway ‘Cryptomus.’ Subscribers can use the proxies to hide their IP addresses and engage in illegal activities, such as DDoS attacks, spamming, and phishing. The malware’s main capability is transforming the infected system into a proxy, which is then used to forward traffic for the subscribers.
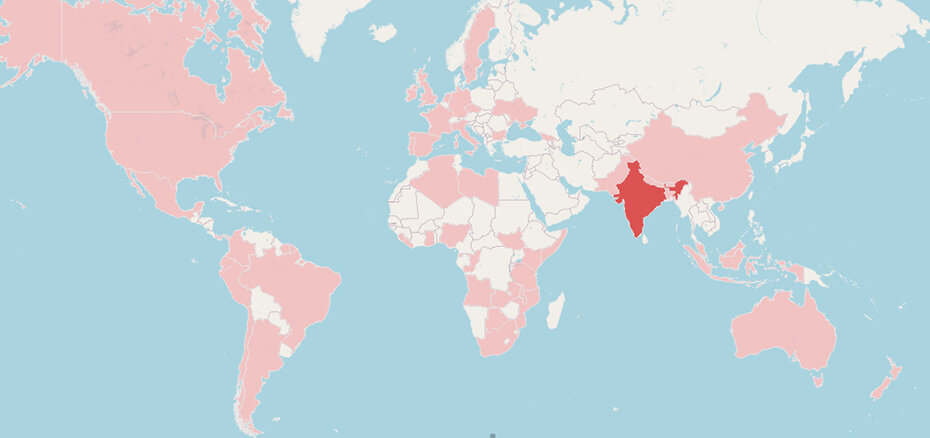
BitSight’s report sheds light on the botnet’s infrastructure, victims, and the proxy service built on top of it. The malware infects computers and turns them into traffic-forwarding proxies for malicious, illegal, or anonymous traffic. It sells this service to subscribers who pay between $1 and $140 per day in crypto to access it. The botnet is distributed by the PrivateLoader and Amadey malware, which are often spread via phishing, exploit kits, malvertizing, trojanized executables downloaded from P2P networks, etc. The geographic distribution is sparse and random, covering the entire globe, but India, the United States, Brazil, Colombia, South Africa, Argentina, and Nigeria count the most infections.
Socks5Systemz
The Socks5Systemz bot is a proxy botnet that is distributed by the PrivateLoader and Amadey malware. These malware loaders are often spread via phishing, exploit kits, malvertizing, trojanized executables downloaded from P2P networks, and other methods. The samples seen by BitSight are named ‘previewer.exe,’ and their task is to inject the proxy bot onto the host’s memory and establish persistence for it via a Windows service called ‘ContentDWSvc.’ The proxy bot payload is a 300 KB 32-bit DLL. It uses a domain generation algorithm (DGA) system to connect with its command and control (C2) server and send profiling info on the infected machine.
The Socks5Systemz botnet has been around since at least 2016, but it has remained relatively under the radar until recently. BitSight’s report sheds light on the botnet’s infrastructure, victims, and the proxy service built on top of it. The geographic distribution is sparse and random, covering the entire globe, but India, the United States, Brazil, Colombia, South Africa, Argentina, and Nigeria count the most infections.
The malware is distributed by the PrivateLoader and Amadey malware, which are often spread via phishing, exploit kits, malvertizing, trojanized executables downloaded from P2P networks, etc. The samples seen by BitSight are named ‘previewer.exe,’ and their task is to inject the proxy bot onto the host’s memory and establish persistence for it via a Windows service called ‘ContentDWSvc.’ The proxy bot payload is a 300 KB 32-bit DLL. It uses a domain generation algorithm (DGA) system to connect with its command and control (C2) server and send profiling info on the infected machine.
As a reaction, the C2 has the capability to issue various commands for execution, including:
- Idle: Take no action.
- Connect: Establish a connection with a backconnect server.
- Disconnect: Sever the connection to the backconnect server.
- Updips: Update the list of permitted IP addresses for sending traffic.
- Upduris: This command is currently not implemented.
The connect command is of particular significance, as it directs the bot to initiate a connection to a backconnect server via port 1074/TCP.
Once linked to the malicious actors’ infrastructure, the compromised device can function as a proxy server and may be offered for sale to other threat actors.
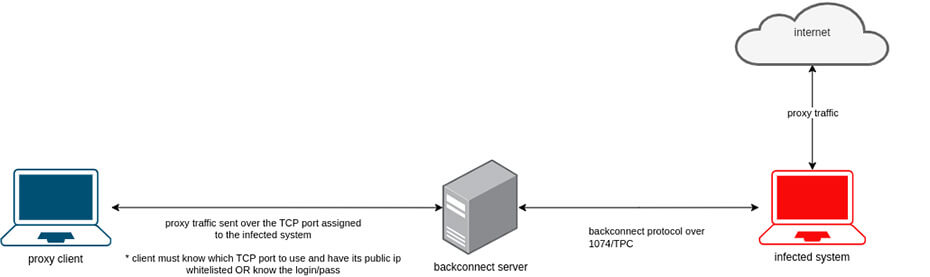
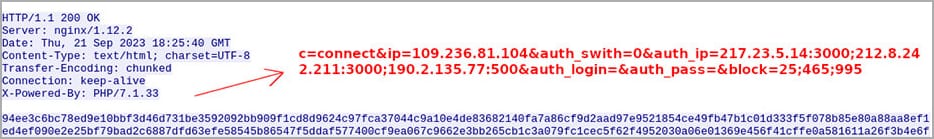
When connecting to the backconnect server, the Socks5Systemz bot uses fields that determine the IP address, proxy password, list of blocked ports, etc. These field parameters ensure that only bots in the allowlist and with the necessary login credentials can interact with the control servers, blocking unauthorized attempts. The bot establishes a backconnect server connection over port 1074/TCP, which allows the infected device to be used as a proxy server and sold to other threat actors.
Illegal business impact
BitSight has mapped an extensive control infrastructure of 53 proxy bot, backconnect, DNS, and address acquisition servers located mainly in France and across Europe (Netherlands, Sweden, Bulgaria). Since the start of October, the analysts recorded 10,000 distinct communication attempts over port 1074/TCP with the identified backconnect servers, indicating an equal number of victims. The geographic distribution is sparse and random, covering the entire globe, but India, the United States, Brazil, Colombia, South Africa, Argentina, and Nigeria count the most infections.
Access to Socks5Systemz proxying services is sold in two subscription tiers, namely ‘Standard’ and ‘VIP,’ for which customers pay via the anonymous (no KYC) payment gateway ‘Cryptomus.’ Subscribers must declare the IP address from where the proxied traffic will originate to be added to the bot’s allowlist. Standard subscribers are limited to a single thread and proxy type, while VIP users can use 100-5000 threads and set the proxy type to SOCKS4, SOCKS5, or HTTP. Prices for each service offering are given below.
The use of proxy services is not new, and it has been exploited by threat actors to carry out various types of nefarious activities. SOCKS5 is an internet protocol that exchanges network packets between a client and server through a proxy server. SOCKS5 optionally provides authentication. SOCKS proxies have been manipulated recently by threat actors to carry out various types of attacks, such as distributed denial-of-service (DDoS) attacks for hire services. The Gwmndy botnet also abused SOCKS proxy servers. Below are the prices for each service offering :
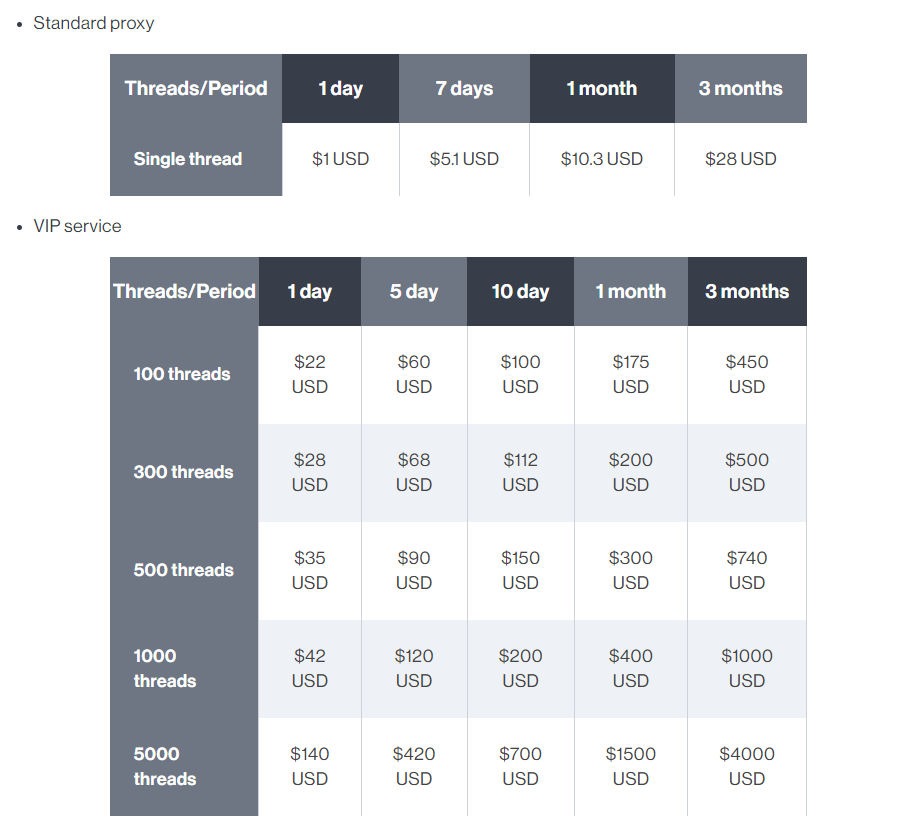
Residential proxy botnets are a lucrative business that has a significant impact on internet security and unauthorized bandwidth hijacking. These services are commonly used for shopping bots and bypassing geo-restrictions, making them very popular. In August, AT&T analysts revealed an extensive proxy network comprising over 400,000 nodes, in which unaware Windows and macOS users were serving as exit nodes channeling the internet traffic of others.
The Socks5Systemz botnet has been around since at least 2016, but it has remained relatively under the radar until recently. BitSight’s report sheds light on the botnet’s infrastructure, victims, and the proxy service built on top of it. The malware infects computers and turns them into traffic-forwarding proxies for malicious, illegal, or anonymous traffic. It sells this service to subscribers who pay between $1 and $140 per day in crypto to access it.
Sources :
https://www.bleepingcomputer.com/news/security/socks5systemz-proxy-service-infects-10-000-systems-worldwide/
https://www.bitsight.com/blog/unveiling-socks5systemz-rise-new-proxy-service-privateloader-and-amadey
https://www.linkedin.com/posts/mekatz_mylobot-investigating-a-proxy-botnet-activity-7030897693115731968-OT85
https://cyber.vumetric.com/security-news/2023/11/05/socks5systemz-proxy-service-infects-10000-systems-worldwide/
https://krebsonsecurity.com/2023/07/who-and-what-is-behind-the-malware-proxy-service-socksescort/
https://www.securonix.com/securonix-threat-research-lab
https://securityintelligence.com/articles/what-is-socks-proxy-exploit/
https://www.zscaler.com/blogs/security-research/dreambus-botnet-technical-analysis
https://en.wikipedia.org/wiki/SOCKS