Microsoft has added a new security feature to its Authenticator app that blocks suspicious notifications during the account login process. The Authenticator app provides multi-factor authentication, password auto-fill, and password-less sign-in to Microsoft accounts. When a user attempts to log in to an account protected by multi-factor authentication (MFA), the app sends a push notification to the user’s device to grant or deny access. The new feature blocks notifications that appear suspicious based on specific checks performed during the account login stage. The Microsoft Authenticator app is available for download on both Android and iOS devices.
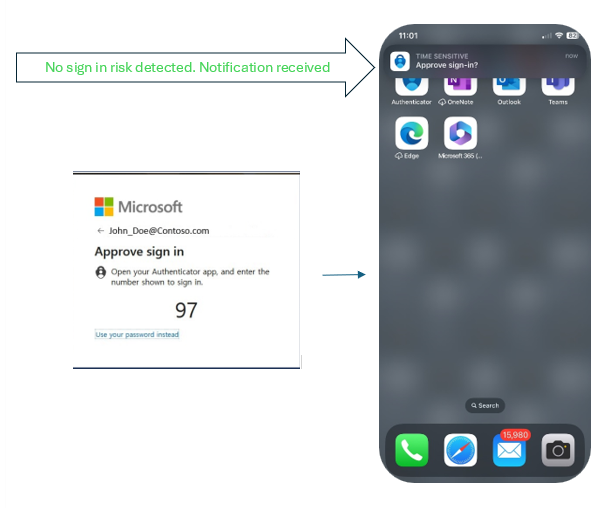
Microsoft has introduced a new feature in its Authenticator app that generates a temporary access code for users to manually log into their account. This feature is an alternative to the push notification feature that hackers often exploit by performing a large number of login attempts for the target account, hoping to frustrate or tire the recipients. If the user approves a request, the attacker gains access to the account and may alter the login protection settings to lock the legitimate user out.
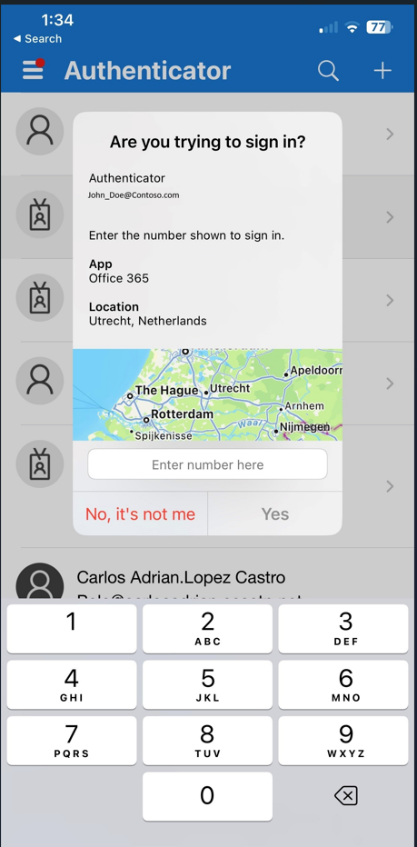
To enhance security, Microsoft introduced “number matching” in May, a mechanism where the user must enter a number displayed on the sign-in screen into their Authenticator app to approve the login. Although this measure has reduced the effectiveness of MFA fatigue attacks, it doesn’t stop the generation of the annoying notifications themselves.
To combat this malicious activity, Microsoft added new features that scrutinize details on login attempts, like if the request comes from an unfamiliar location or shows signs of anomalous activity, to block the notification from showing up. Instead, users receive a message that prompts them to open the Authenticator app and enter a given code. This feature significantly reduces user inconvenience by eliminating irrelevant authentication prompts.
The Microsoft Authenticator app provides multi-factor authentication, password auto-fill, and password-less sign-in to Microsoft accounts. When a user attempts to log in to an account protected by multi-factor authentication (MFA), the app sends a push notification to the user’s device to grant or deny access. The app is available for download on both Android and iOS devices.
Overall, Microsoft is constantly innovating to include enhanced security and experience features in the Authenticator app. The app serves as a repository for all authenticator notifications, ensuring users have a convenient way to retrieve any missed requests. Admins can now better manage their Microsoft Authenticator app features with the refreshed Admin UX and APIs.
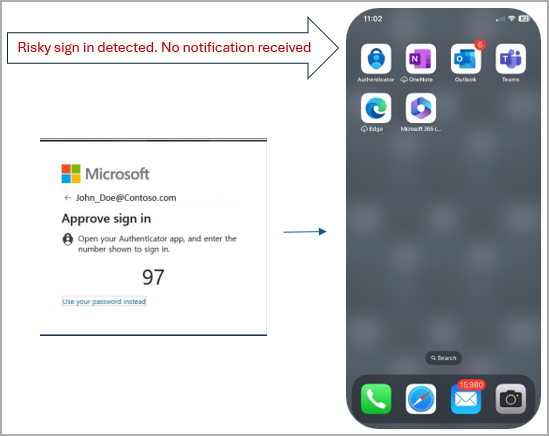
Microsoft Authenticator now blocks suspicious MFA alerts by default, but the login notifications are still generated and made available from within the Authenticator App if the user needs to access and review them. This feature is an alternative to the push notification feature that hackers often exploit by performing a large number of login attempts for the target account, hoping to frustrate or tire the recipients. If the user approves a request, the attacker gains access to the account and may alter the login protection settings to lock the legitimate user out.
Since the roll-out of the new feature completed at the end of September, Microsoft has blocked over six million MFA notifications suspected to have been initiated by hackers. The new security configuration was rolled out in September, allowing users to suppress pop-up notifications for potentially suspicious login requests.
Typically, Microsoft Authenticator users who attempt to log into an account or a service receive a pop-up notification to approve the sign-in request. If Microsoft Authenticator detects anomalous signals in the login attempt, the app will automatically suppress the pop-up notification. Users will be prompted to open the Authenticator app and approve the sign-in request manually. This approach significantly reduces user inconvenience by eliminating irrelevant authentication prompts.
Sources:
https://help.protectedtrust.com/setup-the-microsoft-authenticator-app
https://www.microsoft.com/en-us/security/mobile-authenticator-app
https://apps.apple.com/us/app/microsoft-authenticator/id983156458
https://youtube.com/watch?v=1b_43r6qwk4&t=16
https://support.microsoft.com/en-us/account-billing/download-and-install-the-microsoft-authenticator-app-351498fc-850a-45da-b7b6-27e523b8702a
https://play.google.com/store/apps/details?gl=US&hl=en_US&id=com.azure.authenticator
https://petri.com/microsoft-authenticator-suspicious-mfa-notifications/
https://www.neowin.net/news/microsoft-authenticator-is-now-blocking-suspicious-mfa-phone-notifications-by-default/
https://www.bleepingcomputer.com/news/security/microsoft-authenticator-now-blocks-suspicious-mfa-alerts-by-default/
https://cyber.vumetric.com/security-news/2023/11/07/microsoft-authenticator-now-blocks-suspicious-mfa-alerts-by-default/
https://www.windowscentral.com/software-apps/the-microsoft-authenticator-app-will-suppress-risky-notifications-as-microsoft-pushes-for-improved-security
https://www.it.ox.ac.uk/article/mfa-authenticator-app-update
https://techcommunity.microsoft.com/t5/microsoft-entra-azure-ad-blog/emphasizing-security-by-default-with-advanced-microsoft/ba-p/3773130
https://techcommunity.microsoft.com/t5/microsoft-entra-azure-ad-blog/advanced-microsoft-authenticator-security-features-are-now/ba-p/2365673





