Introduction
OpenSSH is a widely used protocol for secure remote access to servers and systems. It provides encrypted communication and secure authentication, making it an essential component in ensuring the security of network connections. However, recent developments have highlighted a new type of attack known as Terrapin attacks that can downgrade the security of OpenSSH connections.
Understanding Terrapin Attacks
Terrapin is a new attack that can downgrade the security of OpenSSH connections. Researchers from Ruhr University Bochum developed the Terrapin attack, which manipulates sequence numbers during the handshake, allowing attackers to remove or modify messages exchanged through the communication, leading to downgrading the public key algorithms used for user authentication or disabling them. The attack exploits weaknesses in the SSH transport layer protocol in combination with adding that “these have been adopted by a wide range of SSH implementations, therefore affecting a majority of current implementations.” The attack can also be used to exploit vulnerabilities in SSH implementations.
The researchers discovered exploitable implementation flaws in AsyncSSH. The vulnerability (CVE-2023-48795) in the SSH cryptographic network protocol could allow an attacker to downgrade the connection’s security. The researchers have published a Terrapin vulnerability scanner on GitHub, which admins can use to determine if an SSH client or server is vulnerable to the attack. Multiple vendors are gradually mitigating the security problem. One solution is to implement a strict key exchange that makes package injection during the handshake impossible. However, it will take a while for such an issue to be addressed universally. The biggest mitigation factor for the attack is the MitM.
Attack Methodology
Terrapin attacks typically involve the following steps:
- Monitoring the Connection: Attackers intercept the initial connection negotiation between the client and the server. This allows them to understand the encryption algorithms and protocols supported by both parties.
- Forcing Downgrade: Once the initial negotiation is intercepted, attackers manipulate the negotiation process to force the use of weaker encryption algorithms or outdated protocols. This is done through tampering with the exchanged messages or altering the supported algorithms on-the-fly.
- Bypassing Client-side Checks: OpenSSH clients are designed to prefer stronger encryption algorithms by default. However, Terrapin attacks bypass these checks by manipulating the offered algorithms, tricking the client into selecting a weaker encryption algorithm or protocol.
- Exploiting Vulnerabilities: With the security downgraded, attackers can exploit known vulnerabilities in the selected weaker encryption algorithm or protocol. This may include the use of weak keys, susceptibility to eavesdropping, or other weaknesses that compromise the confidentiality and integrity of the communication.
Attack Overview
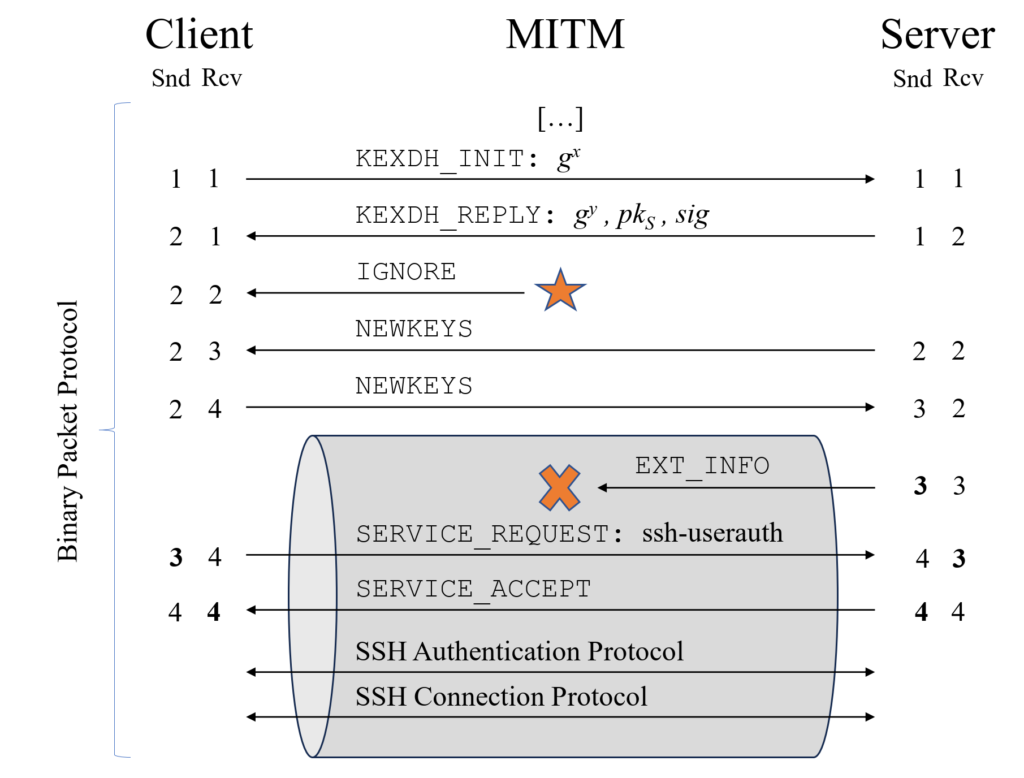
The image shows a practical application of the Terrapin attack. The attacker can drop the EXT_INFO message, used for negotiating several protocol extensions, without the client or server noticing it. Usually, packet deletion would be detected by the client when receiving the next binary packet sent by the server, as sequence numbers would mismatch. To avoid this, an attacker injects an ignored packet during the handshake to offset the sequence numbers accordingly.
Mitigating Terrapin Attacks
To protect against Terrapin attacks and maintain the security of OpenSSH connections, the following countermeasures are recommended:
- Regular Updates: Keep the OpenSSH client and server software up to date with the latest security patches and fixes. These updates often address vulnerabilities that could be exploited by attackers.
- Strict Algorithm Configuration: Configure OpenSSH to only allow secure encryption algorithms and protocols. Remove deprecated or weak algorithms from the configuration to minimize the attack surface.
- Monitoring and Intrusion Detection: Implement monitoring systems that can flag any suspicious activities, such as unexpected changes to the encryption algorithms during the connection negotiation process.
- Encrypted Communication: Whenever possible, establish OpenSSH connections within a trusted network or through a virtual private network (VPN) to ensure end-to-end encryption.
- User Awareness and Education: Educate users about the risks of Terrapin attacks and the importance of verifying the security of their OpenSSH connections. Encourage them to report any suspicious activity or potential security downgrades.
Conclusion
Terrapin attacks pose a significant risk to the security of OpenSSH connections by downgrading encryption algorithms and protocols. Understanding the attack methodology and implementing the recommended countermeasures can greatly enhance the security posture of OpenSSH connections, safeguarding against potential exploitation and unauthorized access. Regular security updates, strict configuration, monitoring, encrypted communication, and user awareness play key roles in mitigating the risks associated with Terrapin attacks.
Sources:
https://terrapin-attack.com/
https://twitter.com/TheCyberSecHub/status/1737157741809184884
https://www.bleepingcomputer.com/news/security/terrapin-attacks-can-downgrade-security-of-openssh-connections/
https://www.helpnetsecurity.com/2023/12/19/ssh-vulnerability-cve-2023-48795/
https://www.reddit.com/r/linux/comments/18lzsys/terrapin_attack_breaks_the_integrity_of_sshs/?rdt=37867
https://arstechnica.com/security/2023/12/hackers-can-break-ssh-channel-integrity-using-novel-data-corruption-attack/
https://cdn.arstechnica.net/wp-content/uploads/2023/12/terrapin-data-attack-800×450.jpg