TeamViewer is a remote access and support software that enables users to access and control devices from their own, allowing for remote desktop access and support. It supports cross-platform connections, including PC to PC, mobile to PC, and PC to mobile, and is compatible with various operating systems such as Windows, Mac OS, Linux, Chrome OS, iOS, and Android. Its features include remote access, file transfer, and screen sharing, making it suitable for remote work, technical support, and collaboration. However, it is important to note that TeamViewer is not designed for monitoring employees or providing stealth monitoring, and users are notified when a remote connection is established. The software works by establishing a connection through a third-party server, allowing users to connect to remote devices via a unique ID assigned by the server[4]. While TeamViewer is a valuable tool for legitimate remote access and support, there have been reported cases of its abuse by cybercriminals, leading some organizations to implement policies to remove and block it from their systems due to security concerns.
Ransomware actors are once again employing TeamViewer as a means to gain initial access to organizational endpoints, with the intention of deploying encryptors based on the leaked LockBit ransomware builder. TeamViewer, a legitimate remote access tool highly utilized in the enterprise world, is valued for its simplicity and capabilities. However, it has also become a favored tool among scammers and ransomware actors, who exploit it to gain access to remote desktops and execute malicious files without hindrance.
This method of utilizing TeamViewer for unauthorized access and subsequent malicious activities is not a new phenomenon. A similar case was initially reported in March 2016, when victims disclosed on the BleepingComputer forums that their devices had been compromised using TeamViewer to encrypt files with the Surprise ransomware. During that period, TeamViewer attributed the unauthorized access to credential stuffing, clarifying that the attackers did not exploit any zero-day vulnerabilities in the software but instead utilized leaked credentials of users.
TeamViewer, being widely deployed, became a prime target for online criminals attempting to log in with compromised account data. Their objective was to determine if there were corresponding TeamViewer accounts with the same credentials. If successful, the attackers could potentially gain access to all assigned devices, enabling them to install malware or ransomware. The software vendor explained at the time that the widespread use of TeamViewer made it a lucrative target for such malicious activities.
TeamViewer targeted again
According to a recent report by Huntress, cybercriminals continue to exploit traditional methods, persisting in the takeover of devices through TeamViewer with the objective of deploying ransomware. The examination of log files, specifically connections_incoming.txt, revealed connections originating from the same source in both instances, suggesting a common attacker.
Upon analyzing the logs of the initial compromised endpoint, Huntress identified multiple accesses by employees, indicating that the software was actively utilized by the staff for legitimate administrative tasks. Contrastingly, the second endpoint under Huntress’s observation, operational since 2018, displayed a lack of activity in the logs for the past three months. This absence of recent activity suggests infrequent monitoring, potentially rendering it a more appealing target for attackers.
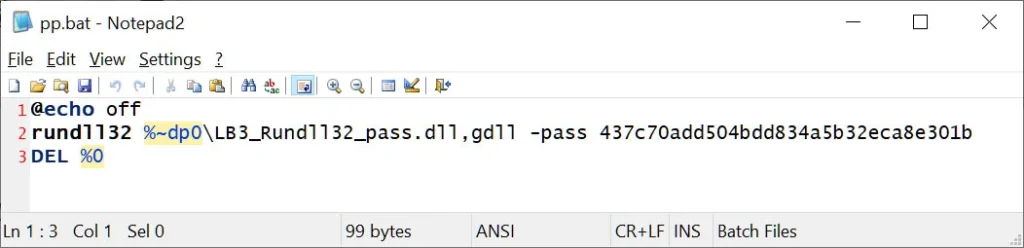
In both scenarios, the attackers sought to deploy the ransomware payload through a DOS batch file (PP.bat) strategically placed on the desktop. This batch file, in turn, executed a DLL file (payload) via a rundll32.exe command, revealing a consistent modus operandi employed by the cybercriminals across the compromised endpoints.
The initial attack on the first endpoint managed to breach security measures but was successfully contained. Conversely, the second endpoint faced a different outcome, as the antivirus product effectively thwarted the attack, compelling the attackers to make repeated attempts at executing the payload without success.
Although Huntress has not definitively attributed these attacks to any known ransomware gangs, they highlight notable similarities to LockBit encryptors generated through a leaked LockBit Black builder. In 2022, the ransomware builder for LockBit 3.0 was leaked, leading to the swift launch of campaigns by the Bl00dy and Buhti gangs utilizing this builder. The leaked builder provides the capability to generate various versions of the encryptor, including an executable, a DLL, and an encrypted DLL that necessitates a password for proper launch.
Analysis of the Indicators of Compromise (IOCs) provided by Huntress indicates that the attacks conducted via TeamViewer seem to employ the password-protected LockBit 3 DLL. While the specific sample identified by Huntress has not been found, an alternative sample detected as LockBit Black appeared on VirusTotal last week. Interestingly, this sample, although categorized as LockBit Black, deviates from the standard LockBit 3.0 ransomware log, indicating that it was created by another ransomware gang taking advantage of the leaked author.
what are some common signs of teamviewer abuse
Some common signs of TeamViewer abuse include:
- Unsolicited phone calls or emails claiming to be from TeamViewer, asking for personal information or access to your device.
- Unauthorized access to your device or network, as evidenced by unusual activity or changes in settings.
- Instances of malware or ransomware being installed on your device without your knowledge or consent.
- Unusual file transfers or unauthorized access to sensitive information.
- Receiving a message that your device is infected with malware, even if it is not.
To protect yourself from TeamViewer abuse, it is essential to maintain strong security measures, such as using complex and unique passwords, keeping software up to date, and being cautious of unsolicited phone calls or emails. Additionally, organizations can implement policies to remove and block TeamViewer from their systems if it is not necessary for their operations.
What are some best practices for securing teamviewer on a network
Some best practices for securing TeamViewer on a network include:
- Disable Random Passwords and Personal Passwords: This ensures that only authorized people can connect to devices.
- Enable Easy Access: This feature allows you to connect to your device without a password, as long as you are logged in to your TeamViewer account. It is more secure than using passwords, as it requires the device ID and password.
- Block and Allowlist: Use your Allowlist and Blocklist to specify who and what can connect to devices with TeamViewer. Blocklist: TeamViewer accounts or device IDs that appear on your device’s Blocklist are blocked from making a connection. Allowlist: TeamViewer accounts or device IDs that appear on your device’s Allowlist are allowed to make a connection.
- Keep TeamViewer updated: Ensure that you have the latest version of TeamViewer installed, as updates often include security improvements and bug fixes.
- Use strong passwords: Passwords should be at least 8 characters long, ideally combining uppercase and lowercase letters, numbers, and special characters.
- Enable Two-Factor Authentication: This adds an extra layer of security to your TeamViewer account.
- Shut down TeamViewer after use: Don’t run TeamViewer sessions in the background and switch to it when needed.
- Use a VPN: A virtual private network (VPN) encrypts data transmission, providing an additional layer of security.
- Verify and update the trusted users list: Regularly review your trusted devices list and remove any that you don’t recognize or that should not have access to the given machine.
- Be cautious of unsolicited phone calls or emails claiming to be from TeamViewer: Report any suspicious activity to the company.
By following these best practices, organizations can reduce the risk of TeamViewer abuse and potential ransomware attacks.
Sources:
https://www.bleepingcomputer.com/news/security/teamviewer-abused-to-breach-networks-in-new-ransomware-attacks/
https://www.teamviewer.com/en-us/unattended-access-security/
https://www.teamviewer.com/en-us/trust-center/security/
https://community.f-secure.com/en/discussion/126516/security-risk
https://community.teamviewer.com/English/kb/articles/108681-best-practices-for-secure-unattended-access
https://www.helpwire.app/blog/teamviewer-security-risk/
https://www.airdroid.com/remote-support/teamviewer-scams/
https://www.reddit.com/r/teamviewer/comments/4m6omd/teamviewer_breach_masterthread_please_post_your/?rdt=63214
https://community.teamviewer.com/English/kb/articles/4715-teamviewer-and-scamming
https://www.linkedin.com/posts/andyprosser_teamviewer-abused-to-breach-networks-in-new-activity-7153954406835605504-9xEM
https://e-crimebureau.com/teamviewer-abused-for-unauthorized-access-and-deploying-lockbit-ransomware/
https://www.reddit.com/r/teamviewer/comments/g2dkcf/what_exactly_can_teamviewer_do_will_i_be_able_to/?rdt=33180
https://blog.invgate.com/what-is-teamviewer
https://community.teamviewer.com/English/kb/articles/33184-what-is-teamviewer
https://superuser.com/questions/661749/how-exactly-does-a-remote-program-like-team-viewer-work