SEO#LURKER campaign
Threat actors are using manipulated search results and fake Google ads to trick users who are searching for legitimate software such as WinSCP into downloading malware instead. Cybersecurity company Securonix is tracking this ongoing activity under the name SEO#LURKER. The malicious advertisement directs the user to a compromised WordPress website gameeweb[.]com, which redirects the user to an attacker-controlled phishing site. The threat actors are believed to leverage Google’s Dynamic Search Ads (DSAs), which automatically generates ads based on a site’s content to serve the malicious ads that take the victims to the infected site. The ultimate goal of the complex multi-stage attack chain is to entice users into clicking on the fake, lookalike WinSCP website, winccp[.]net, and download the malware.
The attack is unique in its way to fingerprint users and distribute time-sensitive payloads. The attack singles out users searching for Notepad++ and PDF converters to serve bogus ads on the Google search results page that, when clicked, filters out bots and other unintended IP addresses by showing a decoy site. People who click on the ad will be redirected via a cloaking service that is meant to filter sandboxes, bots, and anyone not deemed to be a genuine victim. The threat actors have set up a temporary domain at keepasstacking[.]site that performs the conditional redirect to the final destination. The abuse of Punycode is not entirely novel, but combining it with rogue Google Ads is a sign that malvertising via search engines is getting more sophisticated.
The final payload takes the form of a ZIP file (“WinSCP_v.6.1.zip”) that comes with a setup executable, which, when launched, employs DLL side-loading to load and execute a DLL file named python311.dll that’s present within the archive. The researchers said that traffic from the gaweeweb[.]com website to the fake winsccp[.]net website relies on a correct referrer header being set properly. If the referrer is incorrect, the user is ‘Rickrolled’ and is sent to the infamous Rick Astley YouTube video. The researchers also noted that given the fact that the attackers were leveraging Google Ads to disperse malware, it can be believed that the targets are limited to anyone seeking WinSCP software. The geoblocking used on the site hosting the malware suggests that those in the U.S. are victims of this attack.
Attack Chain
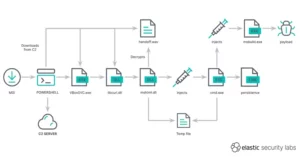
The complex multi-step attack chain involves several steps:

- Users are first directed to a compromised website.
- They are then redirected to a fake website that resembles the legitimate WinSCP site.
- If the referring header is incorrect, users are redirected to a Rick Astley video on YouTube in a tactic known as “Rickrolling.”
- The final payload is a ZIP file containing an installation executable that uses DLL side-loading to execute a malicious DLL file.
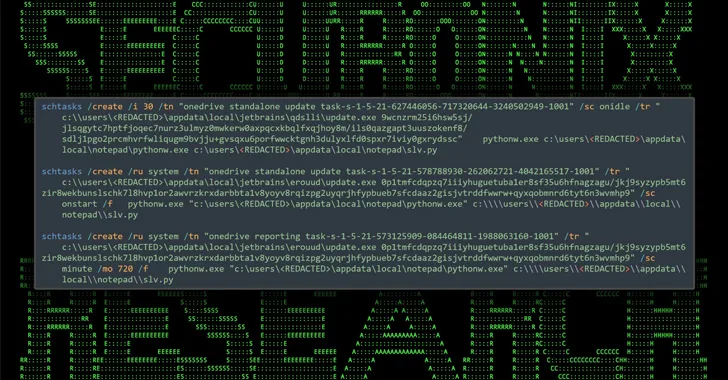
The DLL, for its part, downloads and executes a legitimate WinSCP installer to keep up the ruse, while stealthily dropping Python scripts (“slv.py” and “wo15.py”) in the background to activate the malicious behavior. It’s also responsible for setting up persistence.
Both the Python scripts are designed to establish contact with a remote actor-controlled server to receive further instructions that allow the attackers to run enumeration commands on the host.
“Given the fact that the attackers were leveraging Google Ads to disperse malware, it can be believed that the targets are limited to anyone seeking WinSCP software,” the researchers said.
“The geoblocking used on the site hosting the malware suggests that those in the U.S. are victims of this attack.”
Malware and its impact
The malware, masquerading as a legitimate WinSCP installer, subtly releases Python scripts in the background to trigger malicious behavior and establish contact with a remote server. This allows attackers to execute commands on the host. The malware targets anyone searching for WinSCP software, with a particular focus on users in the United States, as suggested by the geoblocking used on the site hosting the malware.
Growing trend of Malvertising
This incident is not the first time that Google’s Dynamic Search Ads have been abused for malware distribution. Malwarebytes recently reported a similar campaign targeting users searching for PyCharm. The growing trend of malvertising poses a significant threat, as seen in the recent increase in credit card skimming campaigns targeting e-commerce sites.
Late last month, Malwarebytes lifted the lid on a campaign that targets users searching for PyCharm with links to a hacked website hosting a rogue installer that paves the way for the deployment of information-stealing malware.
Malvertising has grown in popularity among cybercriminals in the past few years, with numerous malware campaigns using the tactic for attacks in recent months. Earlier this week, Malwarebytes revealed an uptick in credit card skimming campaigns in October 2023 that’s estimated to have compromised hundreds of e-commerce websites with an aim to steal financial information by injecting convincing counterfeit payment pages.
Call for vigilance
The SEO#LURKER campaign highlights the need for greater vigilance when downloading software from the internet. Users should be wary of search results and advertisements, even when they appear legitimate, as cybercriminals continue to find innovative ways to exploit online platforms for malicious purposes.
Sources:
https://thehackernews.com/2023/11/beware-malicious-google-ads-trick.html?m=1
https://thehackernews.com/2023/10/malvertisers-using-google-ads-to-target.html?m=1
https://www.securonix.com/blog/seolurker-attack-campaign-uses-seo-poisoning-fake-google-ads-to-install-malware/
https://www.linkedin.com/posts/the-cyber-security-hub_beware-malicious-google-ads-trick-winscp-activity-7131275692649897986-p6w8
https://vulners.com/thn/THN:E4061769722AEB49083D2777C54A9D35
https://www.matricedigitale.it/multilingua/pubblicita-google-malware-seolurker/