A recent cybersecurity incident has identified a fresh cyber attack strategy that involves the use of fake MSIX Windows application package files. These malicious files are being used to distribute a new type of malware loader called GHOSTPULSE. The attackers have targeted popular software like Google Chrome, Microsoft Edge, Brave, Grammarly, and Cisco Webex.
MSIX is a Windows application package format that developers can use to bundle, distribute, and install their software on Windows systems. According to Elastic Security Labs researcher Joe Desimone, who published a technical report last week, MSIX relies on access to legitimately acquired or stolen code signing certificates, which makes it an attractive option for groups with substantial resources.
The choice of bait in the form of installer files suggests that individuals or organizations being targeted may be lured into downloading the MSIX packages using well-established tactics, including compromised websites, search engine optimization (SEO) manipulation, or malicious advertising.
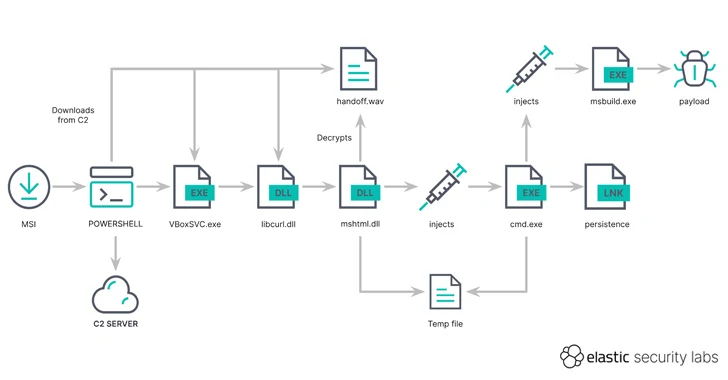
When the MSIX file is executed, a Windows prompt appears, prompting users to click the “Install” button. Doing so initiates the covert download of GHOSTPULSE onto the compromised computer from a remote server located at “manojsinghnegi[.]com” via a PowerShell script.
This operation unfolds across several phases, starting with an initial payload encapsulated within a TAR archive file. This payload consists of an executable designed to mimic the Oracle VM VirtualBox service (VBoxSVC.exe), which, in fact, is a valid binary bundled with Notepad++ (gup.exe).
Within the TAR archive, you can also find a file named handoff.wav and a modified version of libcurl.dll that’s tampered with to progress the infection process further. This manipulation leverages the vulnerability of gup.exe to load the altered libcurl.dll, thus facilitating the next stage of the infection via DLL side-loading.
Desimone explained that the PowerShell script initiates the execution of the VBoxSVC.exe binary, which then sideloads the malicious DLL, libcurl.dll, from the current directory. This approach aims to keep the encrypted malicious code’s presence on the disk to a minimum, allowing it to evade detection by file-based antivirus and machine learning scans.
Subsequently, the tampered DLL proceeds by analyzing the handoff.wav file, which contains an encrypted payload. This payload is decoded and executed via mshtml.dll using a technique called module stomping. This process ultimately leads to the activation of GHOSTPULSE.
GHOSTPULSE functions as a loader and employs another method called process doppelgänging to kickstart the execution of the final malware. This includes a variety of malicious software such as SectopRAT, Rhadamanthys, Vidar, Lumma, and NetSupport RAT.
Sources :
https://thehackernews.com/2023/10/hackers-using-msix-app-packages-to.html




