Apple’s “Find My” location network is designed to help users locate lost or misplaced Apple devices, including iPhones, iPads, Macs, Apple Watches, AirPods, and Apple Tags. The service relies on GPS and Bluetooth data crowd-sourced from millions of Apple devices worldwide to find devices reported as lost or stolen, even if those are offline. Lost devices send Bluetooth signals in a constant loop detected by nearby Apple devices, which then anonymously relay their location to the owner through the Find My network.
However, researchers at Positive Security have discovered that malicious actors could abuse the Find My network to transmit sensitive information captured by keyloggers installed in keyboards. The potential to abuse Find My to transmit arbitrary data besides just device location was first discovered by Positive Security researchers Fabian Bräunlein and his team over two years ago, but apparently, Apple addressed this problem.
The analysts have even published their implementation on GitHub, called ‘Send My,’ which others can leverage for uploading arbitrary data onto Apple’s Find My network and retrieving it from any internet-enabled device anywhere in the world.
Apple has been working closely with various safety groups and law enforcement agencies to prevent unwanted tracking and misuse of their products. They have identified even more ways to update AirTag safety warnings and help guard against further unwanted tracking. Apple has also been working on advancements coming to AirTag and the Find My network to provide a great experience, but also with safety and privacy in mind.
In summary, Apple’s “Find My” location network can be abused by malicious actors to stealthily transmit sensitive information captured by keyloggers installed in keyboards. However, Apple has been working to address this problem and improve the safety and privacy of their products.
Relaying arbitrary data
Researchers at Positive Security have discovered that malicious actors could abuse the Find My network to transmit sensitive information captured by keyloggers installed in keyboards. To better highlight the risk to the public, they created a proof-of-concept hardware device. They integrated a keylogger with an ESP32 Bluetooth transmitter into a USB keyboard to show that it’s possible to relay passwords and other sensitive data typed on the keyboard through the Find My network via Bluetooth.
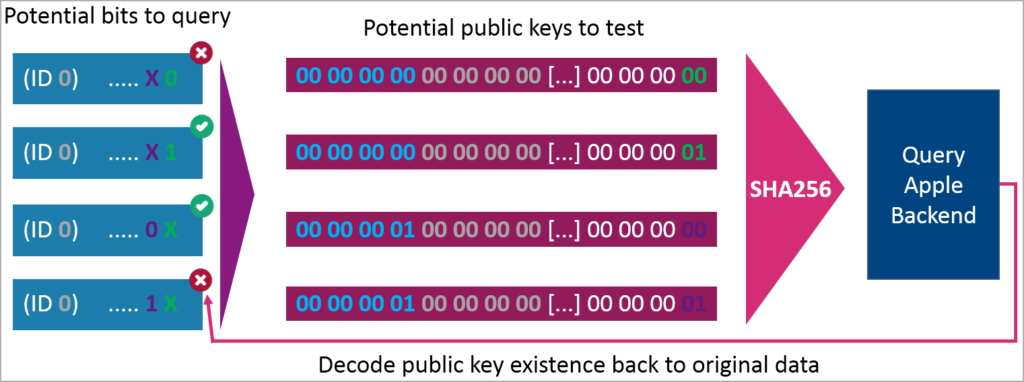
The keylogger doesn’t have to use an AirTag or an officially supported chip, as Apple devices are tuned to respond to any Bluetooth message. If that message is appropriately formatted, the receiving Apple device will create a location report and upload it to the Find My network. The sender needs to create many slightly different public encryption keys simulating multiple AirTags and encode arbitrary data into the location reports. Bluetooth transmission is far stealthier than WLAN keyloggers or Raspberry Pi devices that can be easily noticed in well-guarded environments, and the Find My platform can covertly leverage omnipresent Apple devices for the relay.
It is important to protect yourself from keylogger attacks used by malicious users. Because keyloggers can record and quickly identify sensitive information, they are a significant threat to cybersecurity. To protect yourself, it’s important to know what keyloggers are, how to prevent an attack and how to remove a keylogger if you are attacked. Keyloggers are tools that can record every keystroke that you type into a computer or mobile keyboard. Because you interact with a device primarily through the keyboard, keyloggers can record a lot of information about your activity. For example, keyloggers can track credit card information that you enter, websites you visit and passwords you use.
In summary, researchers at Positive Security have created a proof-of-concept hardware device to show that it’s possible to relay passwords and other sensitive data typed on the keyboard through the Find My network via Bluetooth. This highlights the risk to the public and the importance of protecting oneself from keylogger attacks.
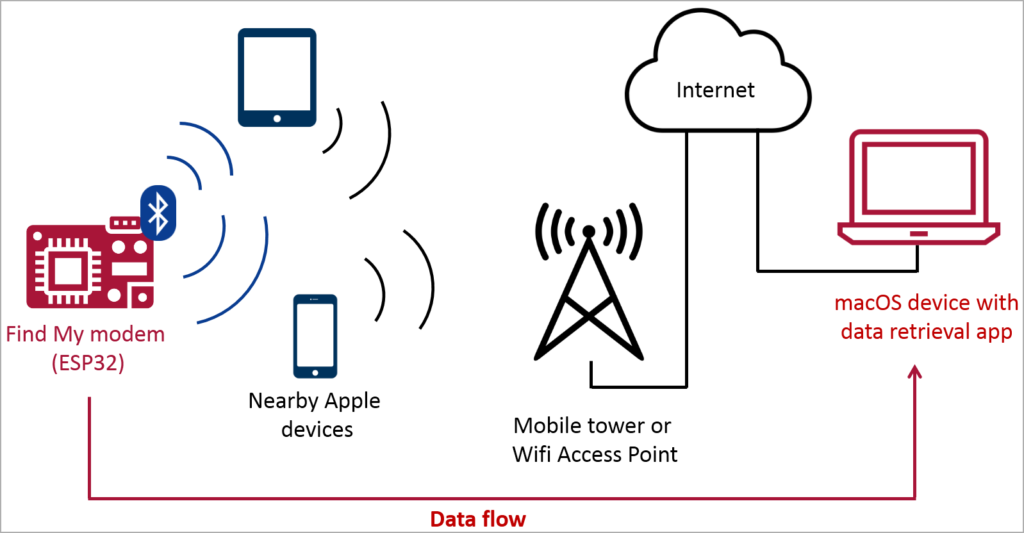
The application consists of two parts:
- Firmware: An ESP32 firmware that turns the microcontroller into a serial (upload only) modem
- DataFetcher: A macOS application used to retrieve, decode and display the uploaded data
Both are based on OpenHaystack, an open source implementation of the Find My Offline Finding protocol.
Bluetooth transmission is a stealthier way to transmit sensitive information captured by keyloggers installed in keyboards than WLAN keyloggers or Raspberry Pi devices that can be easily noticed in well-guarded environments. The Find My platform can covertly leverage omnipresent Apple devices for the relay. The keylogger doesn’t have to use an AirTag or an officially supported chip, as Apple devices are tuned to respond to any Bluetooth message. If that message is appropriately formatted, the receiving Apple device will create a location report and upload it to the Find My network.
The sender needs to create many slightly different public encryption keys simulating multiple AirTags and encode arbitrary data into the keys by assigning specific bits at predetermined positions in the keys. This way, the multiple reports retrieved from the cloud can be concatenated and decoded at the receiving end to retrieve the arbitrary data, in this case, the keylogger’s captures. The total cost of the data-siphoning contraption was roughly $50, using a Bluetooth-enabled version of the ‘EvilCrow’ keylogger and a standard USB keyboard.
There are various hardware keyloggers that are plugged in between the USB keyboard and the computer and are invisible to virus protection programs. Such devices store keyboard records in their internal memory and could in many cases also transmit the tapped data to the attacker via Wi-Fi – at least in theory. To protect oneself from keylogger attacks, it is important to know what keyloggers are, how to prevent an attack, and how to remove a keylogger if you are attacked.
The sender needs to create multiple slightly different public encryption keys that simulate several AirTags and encode arbitrary data into these keys by setting specific bits at predefined positions within the keys.
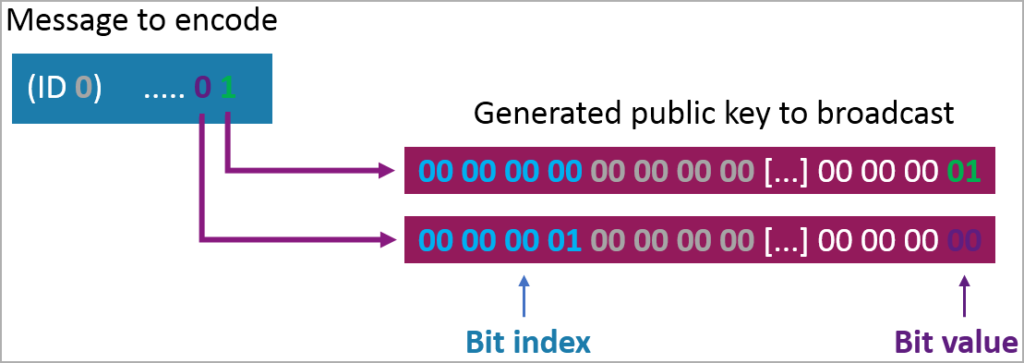
By following this approach, it is possible to combine and decode the various reports obtained from the cloud when they reach the recipient, allowing for the retrieval of the arbitrary data, which, in this scenario, refers to the keylogger’s captured information.
According to Bräunlein, the total cost of the data-siphoning contraption was approximately $50. The researchers integrated a keylogger with an ESP32 Bluetooth transmitter into a USB keyboard to show that it’s possible to relay passwords and other sensitive data typed on the keyboard through the Find My network via Bluetooth.

The PoC attack achieved a transmission rate of 26 characters per second and a reception rate of 7 characters/sec, with a latency of between 1 and 60 minutes, depending on the presence of Apple devices at the keylogger’s range. While this may not be very fast, waiting for several hours or even days wouldn’t be a deal-breaker for malicious actors if recovering valuable information such as passwords is the goal. The best part is that Apple’s anti-tracking protections that notify users Air Tags might be tracking them are not activated by the stationary keylogger inside the keyboard, so the device remains hidden and unlikely to be discovered.
There are various keystroke encryption tools available that can help protect against keylogger attacks, such as SpyShelter Anti-Keylogger and KeyScrambler. These tools encrypt keystrokes in real-time, making it difficult for keyloggers to record sensitive information. Another way to protect oneself is to disable Bluetooth when not in use, as this can prevent attackers from using the Find My network to transmit sensitive information.
Sources :
https://www.keelog.com
https://www.linkedin.com/posts/tony-hynes_signal-says-there-is-no-evidence-rumored-activity-7119762067561086976-nJzz?trk=public_profile_share_view[6] https://www.crowdstrike.com/cybersecurity-101/attack-types/keylogger/
https://www.bleepingcomputer.com/news/apple/apple-find-my-network-can-be-abused-to-steal-keylogged-passwords/
https://malwaretips.com/threads/apple-find-my-network-can-be-abused-to-steal-keylogged-passwords.126951/
https://isp.page/news/apple-find-my-network-can-be-abused-to-steal-keylogged-passwords/
https://lemmy.world/post/7860568
https://www.heise.de/news/Keylogger-keyboard-leaks-passwords-via-Apple-s-Find-My-location-network-9344806.html
https://www.apple.com/newsroom/2022/02/an-update-on-airtag-and-unwanted-tracking/