Researchers at Eurecom have developed six new attacks collectively named ‘BLUFFS’ that can compromise the confidentiality of Bluetooth sessions, enabling device impersonation and man-in-the-middle (MitM) attacks. Daniele Antonioli, the discoverer of these attacks, has elucidated that BLUFFS exploits two previously unknown flaws in the Bluetooth standard concerning the derivation of session keys for decrypting data during communication. These flaws are not specific to hardware or software configurations but are architectural in nature, affecting Bluetooth at a fundamental level. The identified issues are tracked under the identifier CVE-2023-24023 and impact Bluetooth Core Specification 4.2 through 5.4. Given the widespread use of Bluetooth across various devices, including laptops, smartphones, and other mobile devices, the potential impact of BLUFFS is significant, as it could affect billions of devices.
Eurecom, where the researchers are based, is a renowned institution known for its research in digital security, data science, and communication systems. The institution’s research program is supervised by the Scientific Council, and it emphasizes transdisciplinary activities at the intersection of these research areas, such as security in 5G, AI and communication systems, and AI and digital security. This focus on digital security aligns with the nature of the BLUFFS attacks, which target a fundamental security aspect of Bluetooth technology.
The impact of these attacks is not limited to a specific subset of devices, as the identified flaws affect Bluetooth at an architectural level, potentially impacting billions of devices across different versions of the Bluetooth Core Specification. This underscores the significance of the research conducted at Eurecom, which aims to address fundamental security challenges in wireless communication systems.
How BLUFFS works
BLUFFS represents a collection of exploits strategically designed to target Bluetooth, with the primary objective of undermining the forward and future secrecy of Bluetooth sessions. By doing so, BLUFFS seeks to compromise the confidentiality of both past and forthcoming communications between connected devices.
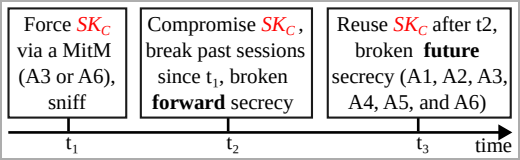
The exploitation strategy employed by BLUFFS hinges on identifying and capitalizing on four specific vulnerabilities within the session key derivation process. Notably, two of these vulnerabilities are newly discovered, adding a layer of sophistication to the attack. The ultimate goal is to exploit these flaws in a manner that compels the derivation of a short, inherently weak, and easily predictable session key (SKC).
Following the successful exploitation of the vulnerabilities, the attacker proceeds to employ brute-force techniques to decipher the compromised key. This pivotal step grants them the capability to decrypt historical communications, thereby exposing sensitive information from past interactions. Additionally, the attacker gains the ability to decrypt ongoing or manipulate future communications, posing a significant threat to the overall security and integrity of the Bluetooth-enabled devices involved in the communication process.
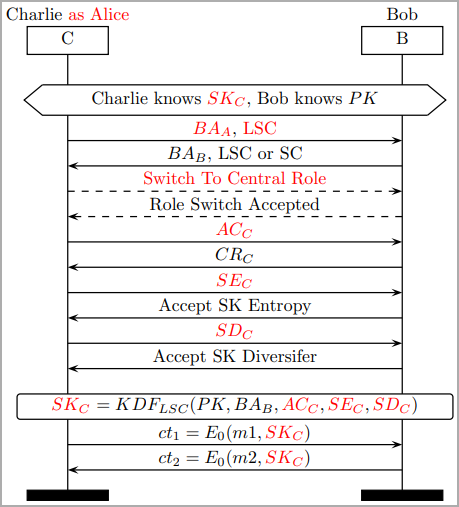
The successful execution of this attack relies on the condition that the perpetrator is situated within Bluetooth range of the two specific targets engaged in data exchange. In order to carry out the exploit, the attacker assumes the role of one of the targets, engaging in an impersonation strategy. The objective is to initiate negotiations with the other target, advocating for the establishment of a weakened session key. This entails proposing the lowest conceivable key entropy value during the negotiation process. Additionally, the attacker employs a constant session key diversifier to further manipulate the derivation of the session key.
To break down the process further, the attacker strategically positions themselves within the proximity required for Bluetooth communication between the targeted devices. By assuming the identity of one of the devices engaged in the data exchange, the attacker can then manipulate the negotiation phase. This involves advocating for a session key with diminished strength by suggesting the lowest possible key entropy value. Simultaneously, the use of a constant session key diversifier introduces an additional layer of control, contributing to the overall success of the attack. This intricate maneuver allows the attacker to influence and guide the session key derivation towards a weakened and more predictable state, thereby facilitating the subsequent stages of the exploit.
The documentation introduces six distinct categories of BLUFFS attacks in the published paper, encompassing a range of attack scenarios involving impersonation and Man-in-the-Middle (MitM) techniques. Notably, these attacks remain viable irrespective of whether the targeted victims support Secure Connections (SC) or Legacy Secure Connections (LSC).
As part of their research efforts, the scholars have meticulously crafted and made available a comprehensive toolkit on GitHub, serving as a practical demonstration of BLUFFS’ efficacy. This toolkit incorporates essential elements such as a Python script designed for testing the various attacks, ARM patches for implementation, a parser for data analysis, and PCAP samples extracted from the tests conducted by the researchers. The toolkit essentially provides a hands-on resource for users to explore, understand, and validate the vulnerabilities associated with BLUFFS, contributing to a deeper comprehension of the potential risks posed by these exploits in real-world Bluetooth communication scenarios.
Impact and remediation
BLUFFS poses a significant threat to the security of Bluetooth technology, affecting Bluetooth 4.2, initially introduced in December 2014, and continuing to impact all subsequent versions, including the latest iteration, Bluetooth 5.4, released in February 2023.
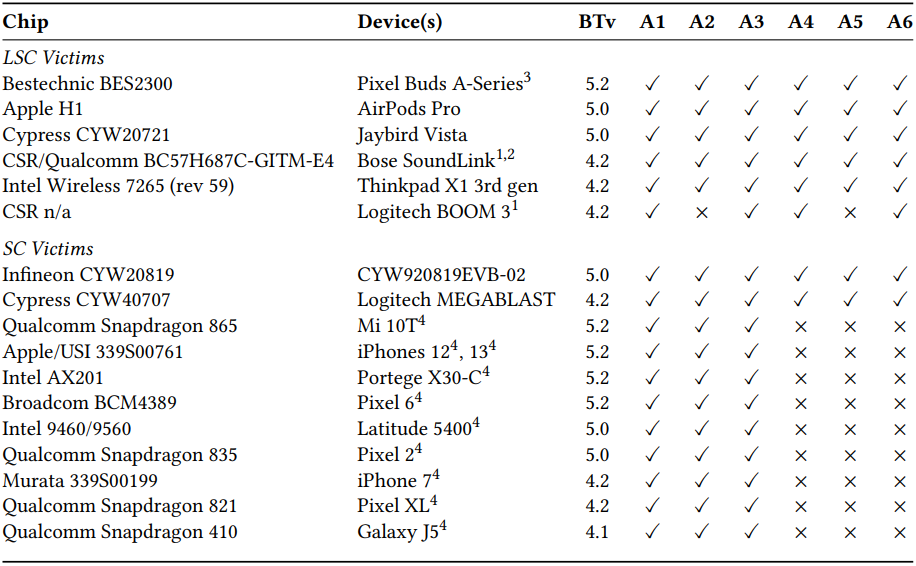
The research paper from Eurecom provides a comprehensive examination of BLUFFS by conducting tests across a diverse array of devices. These devices include smartphones, earphones, and laptops, all running various Bluetooth versions ranging from 4.1 to 5.2. The findings revealed a concerning pattern, as every tested device demonstrated vulnerability to a minimum of three out of the six distinct BLUFFS attacks. This widespread susceptibility underscores the pervasive nature of the security risks introduced by BLUFFS across a broad spectrum of Bluetooth-enabled products, highlighting the urgent need for robust countermeasures to mitigate potential breaches in communication security.
The paper additionally puts forth a set of backward-compatible modifications aimed at fortifying session key derivation processes and mitigating vulnerabilities posed by BLUFFS and analogous threats. One proposed enhancement involves the introduction of a novel “Key Derivation Function” (KDF) tailored for Legacy Secure Connections (LSC). This modification incorporates a mutual nonce exchange and verification mechanism, introducing minimal overhead while bolstering the security of the connection.
Another recommended modification advocates for the adoption of a shared pairing key to facilitate mutual authentication of key diversifiers. This measure serves to validate the legitimacy of session participants, contributing to an additional layer of security in the communication process. Furthermore, the proposal urges the enforcement of Secure Connections (SC) mode wherever feasible and underscores the importance of maintaining a cache of session key diversifiers to prevent instances of key reuse.
In response to the identified vulnerabilities, Bluetooth SIG, the non-profit organization overseeing the development and licensing of Bluetooth technology, has received and acknowledged the report from Eurecom. The organization has released an official statement on its website, suggesting practical measures to enhance security. Recommendations include implementing connection rejections for low key strengths below seven octets, utilizing ‘Security Mode 4 Level 4’ for heightened encryption strength, and opting for ‘Secure Connections Only’ mode during pairing processes. These proactive measures aim to address and minimize the potential impact of security threats within the Bluetooth ecosystem.
Sources :
https://www.bleepingcomputer.com/news/security/new-bluffs-attack-lets-attackers-hijack-bluetooth-connections/
https://www.eurecom.fr/en/research
https://web.cs.ucdavis.edu/~zubair/files/Dr-Shehroze-Farooqi.pdf
https://www.usenix.org/system/files/login/articles/login_dec14_sec14_report.pdf