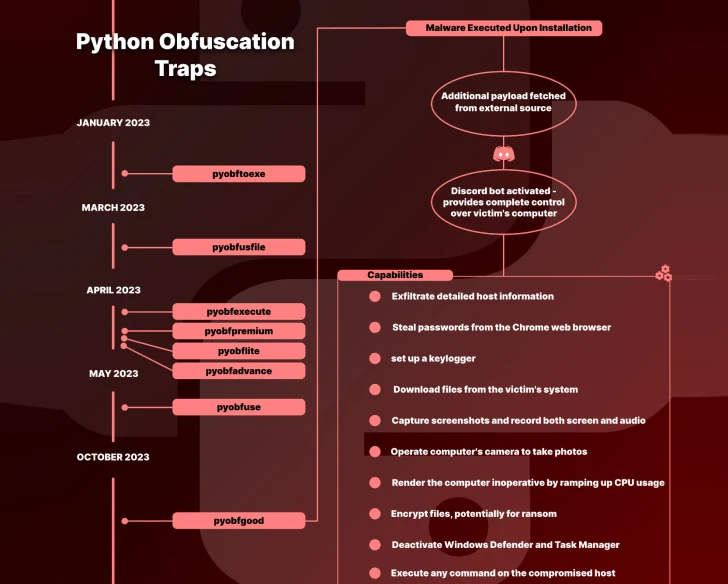
A new set of malicious Python packages has been discovered on the Python Package Index (PyPI) repository. The packages are designed to steal sensitive information from compromised developer systems. The packages are disguised as seemingly innocuous obfuscation tools, but they contain a piece of malware called BlazeStealer, which retrieves an additional malicious script from an external source. This enables a Discord bot that gives attackers complete control over the victim’s computer. The malware is designed to steal Windows users’ application credentials, personal data, and tracking information for their cryptocurrency wallets.
PyPI is the official repository of Python software packages and is widely used by developers to find and install useful libraries and tools for their projects. Unfortunately, its popularity makes it an attractive target for threat actors targeting developers or their projects. PyPI doesn’t have the resources to scrutinize all package uploads, so it relies on user reports to find and remove malicious files. By the time they are deleted, though, the bad packages usually count several hundred downloads.
The malicious packages discovered on PyPI are intended to steal application credentials, personal data, and cryptocurrency wallet information. The packages lack an associated GitHub repository, which is commonly found with legitimate packages. This could indicate a desire to hide the code from view. This, coupled with a limited number of downloads, further raises suspicions.
The malware campaign is a reminder that developers should be vigilant when installing packages from PyPI. They should verify the authenticity of packages and use trusted sources when installing dependencies. In addition, organizations should implement security measures such as automated scanning and monitoring to detect and prevent attacks in their software supply chain.
The campaign began in January 2023 and involves eight packages named Pyobftoexe, Pyobfusfile, Pyobfexecute, Pyobfpremium, Pyobflite, Pyobfadvance, Pyobfuse, and pyobfgood. These packages contain setup.py and init.py files that retrieve a Python script hosted on transfer[.]sh, which is executed immediately upon installation. The malware, called BlazeStealer, runs a Discord bot that enables the threat actor to harvest a wide range of information, including passwords from web browsers and screenshots, execute arbitrary commands, encrypt files, and deactivate Microsoft Defender Antivirus on the infected host.
The discovery of malicious packages on PyPI is not new. In March 2023, researchers discovered six malicious packages on PyPI targeting Windows users. The packages were intended to steal application credentials, personal data, and cryptocurrency wallet information. In January 2023, Fortinet discovered three malicious packages on PyPI that carried code to drop info-stealing malware on developers’ systems. In February 2023, security firm Phylum discovered more than 400 malicious packages on PyPI that contained almost identical malicious payloads. In May 2023, administrators of PyPI temporarily disabled new user sign-ups and package uploads due to the volume of malicious users and projects being created on the index. In June 2023, more than 45,000 users fell victim to malicious PyPI packages.
The recent discovery of BlazeStealer in PyPI packages is a reminder of the importance of cybersecurity in the software development process. Developers and organizations should take steps to protect themselves from these types of attacks, including verifying the authenticity of packages and implementing security measures to detect and prevent attacks in their software supply chain. PyPI should also consider implementing more stringent security measures to prevent malicious packages from being uploaded to the repository.
Moreover, it has the potential to make the computer inoperable by increasing CPU usage, embedding a Windows Batch script in the startup directory for machine shutdown, and even causing a blue screen of death (BSoD) error.
“It makes sense that developers employing code obfuscation are likely handling valuable and sensitive information, making them an attractive target for hackers,” Gelb pointed out.
The majority of downloads linked to these malicious packages originated from the U.S., with China, Russia, Ireland, Hong Kong, Croatia, France, and Spain following. Collectively, they were downloaded 2,438 times before removal.
“While the open-source domain is a breeding ground for innovation, caution is essential,” Gelb emphasized. “Developers need to stay alert and thoroughly vet packages before incorporating them.”
Sources :
https://unit42.paloaltonetworks.com/malicious-packages-in-pypi/
https://arstechnica.com/information-technology/2023/02/451-malicious-packages-available-in-pypi-contained-crypto-stealing-malware/
https://thehackernews.com/2023/06/malicious-pypi-packages-using-compiled.html?m=1
https://blog.sonatype.com/top-8-malicious-attacks-recently-found-on-pypi
https://www.bleepingcomputer.com/news/security/malicious-lolip0p-pypi-packages-install-info-stealing-malware/
https://cyble.com/blog/over-45-thousand-users-fell-victim-to-malicious-pypi-packages/