In a recent surge of BazarCall attacks, cybercriminals have adopted a novel approach by utilizing Google Forms to generate and dispatch payment receipts to their unsuspecting victims. This innovative tactic is designed to enhance the perceived legitimacy of the phishing attempt, thereby increasing the likelihood of success.
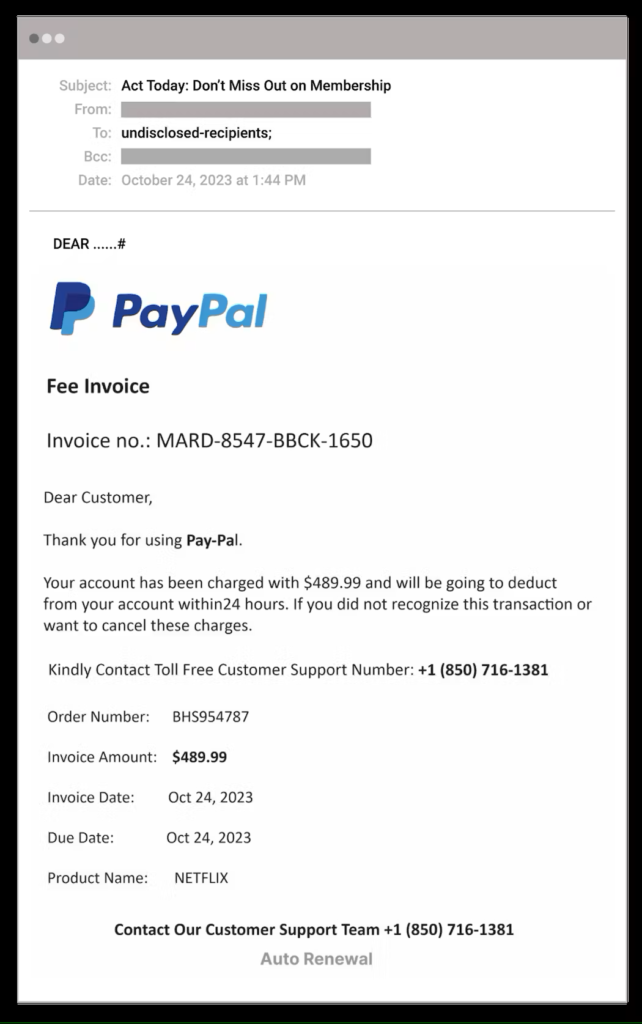
First identified in 2021, BazarCall is a phishing attack that employs deceptive emails resembling payment notifications or subscription confirmations from reputable entities such as security software providers, computer support services, and popular streaming platforms. These fraudulent emails typically convey a sense of urgency, claiming that the recipient is about to be automatically enrolled in an exorbitantly priced subscription. The recipient is then urged to cancel the subscription promptly if they wish to avoid being charged.
Notably, the traditional modus operandi of these phishing emails involved providing a phone number rather than a hyperlink. This number purportedly connected victims to a customer service agent affiliated with the impersonated brand. Victims, upon dialing the number, would unknowingly engage with a cybercriminal posing as a customer support representative. This deceptive interaction was aimed at coaxing victims into unwittingly installing malware on their computers through a step-by-step process.
The malware responsible for these attacks is known as BazarLoader, aptly named for its function as a tool designed to facilitate the installation of additional malicious payloads on the victim’s system. The integration of Google Forms into the attack methodology represents a strategic evolution in the pursuit of a more convincing and effective phishing campaign.
The attack process involves the following steps:
- The attacker creates a Google Form with details about a fake transaction, such as the invoice number, date, payment method, and miscellaneous information about the product or service used as bait.
- The attacker enables the response receipt option on the Settings tab and sends the invitation to complete the form.
- When the invitation arrives, the attacker clicks the “Fill Out Form” button, which opens the Google Form.
This attack is difficult to detect for several reasons:
- There are no clear indicators of compromise, such as a malicious link or attachment, making it challenging for legacy email security systems to flag or block the phishing email.
- Google Forms is a widely used and legitimate service for creating surveys, quizzes, and forms, making it difficult for email security tools to distinguish between legitimate and malicious forms.
- Google Forms often uses dynamically generated URLs, which constantly change and can evade traditional security measures that rely on known patterns to identify threats.
To protect yourself from BazarCall attacks, it is essential to be cautious when receiving emails with payment requests or links to unfamiliar websites, especially if they come from unknown sources or seem suspicious. Additionally, using strong email security tools can help detect and block potential threats before they reach your inbox.
Abuse of Google Forms
Abnormal, an email security firm, has recently identified a novel iteration of the BazarCall attack, marking a concerning trend in the abuse of Google Forms. Google Forms, a widely used free online tool, allows users to create personalized forms and quizzes that can be shared, integrated into websites, and utilized for various purposes.
In this modified attack, the perpetrator crafts a Google Form containing fabricated details of a non-existent transaction, including elements such as invoice number, date, payment method, and miscellaneous information related to the purported product or service. Subsequently, the attacker activates the “response receipt” feature in the form settings, triggering the automatic dispatch of a completed form copy to the provided email address.
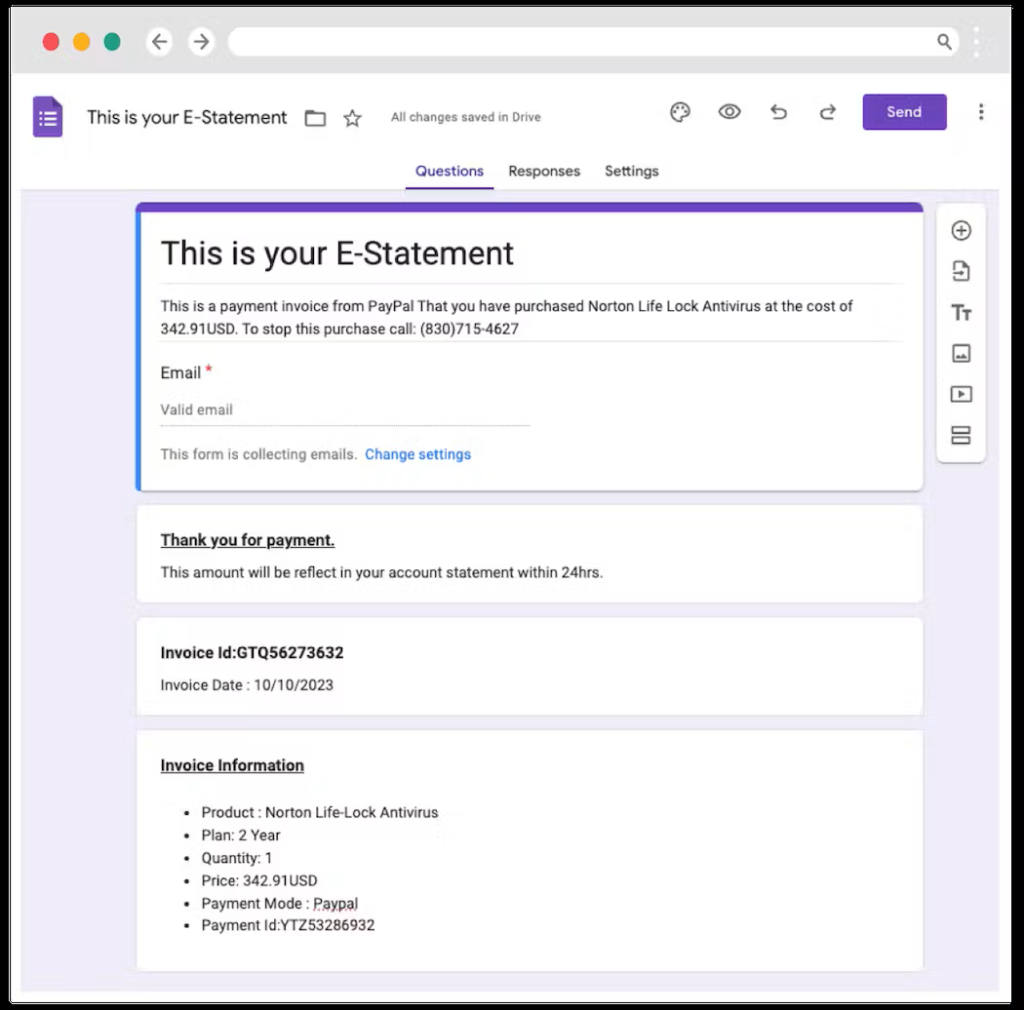
Utilizing the target’s email address, a counterfeit payment confirmation, resembling a legitimate transaction, is sent from Google’s servers to the unsuspecting recipient. Due to the genuine nature of Google Forms, conventional email security tools are unable to flag or block these phishing emails, ensuring their successful delivery to the intended targets. Adding to the illusion of authenticity, the email originates from a Google address, specifically “noreply@google.com.”
The fraudulent invoice sent to the victim incorporates the threat actor’s phone number, accompanied by an urgent directive for recipients to call within 24 hours to address any disputes. This element of urgency enhances the likelihood of successful manipulation. While Abnormal’s report does not delve into the subsequent stages of the attack, it is worth noting that BazarCall has been previously associated with gaining initial access to corporate networks, often paving the way for ransomware attacks.
Citations:
https://abnormalsecurity.com/blog/bazarcall-attack-leverages-google-forms
https://cyber.vumetric.com/security-news/2023/12/13/bazarcall-attacks-abuse-google-forms-to-legitimize-phishing-emails/
https://www.bleepingcomputer.com/news/security/bazarcall-attacks-abuse-google-forms-to-legitimize-phishing-emails/
https://thehackernews.com/2023/12/bazacall-phishing-scammers-now.html?m=1
https://itnerd.blog/2023/12/13/new-bazarcall-attack-variant-discovered-threat-actors-leverage-google-form-with-call-back-phishing/?amp=1
https://intersys.co.uk/wp-content/uploads/Phishing-email-graphic-scaled.jpg





