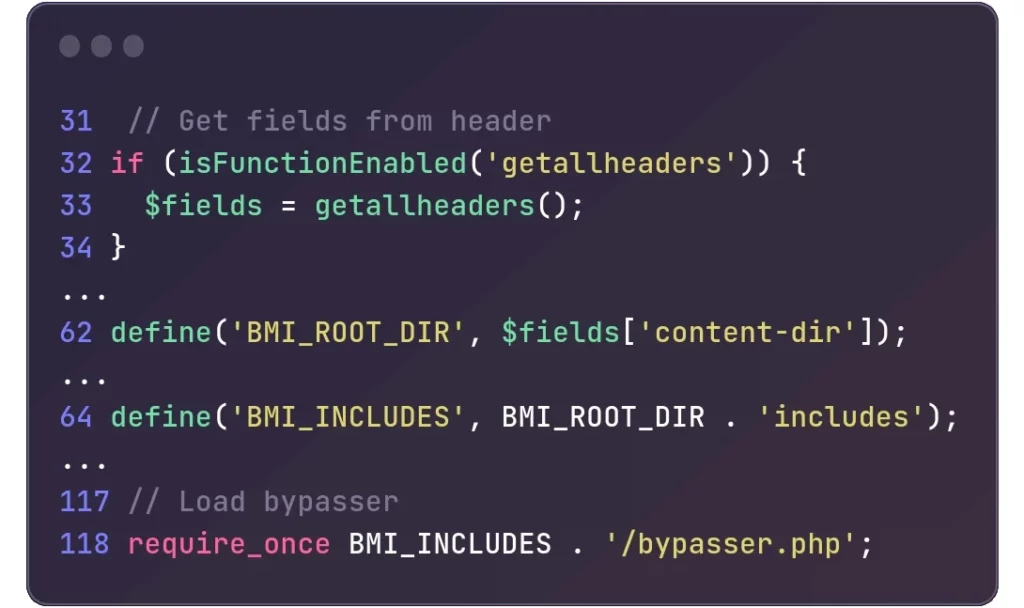
A critical vulnerability has been discovered in the Backup Migration plugin for WordPress, which has more than 90,000 installations. The vulnerability, tracked as CVE-2023-6553 and rated with a 9.8/10 severity score, allows unauthenticated attackers to gain remote code execution (RCE) and take over targeted websites. The vulnerability was discovered by the Nex Team, who reported it to WordPress security firm Wordfence under a recently launched bug bounty program. The vulnerability impacts all plugin versions up to and including Backup Migration 1.3.6, and malicious actors can exploit it in low-complexity attacks without user interaction. Attackers can inject and execute arbitrary PHP code using a flaw in Backup Migration, which has been downloaded more than 90,000 times. The vulnerability arises from “an attacker being able to control the values passed to an include, and subsequently leverage that to achieve remote code-execution,” according to a post on the Wordfence site. Specifically, line 118 within the /includes/backup-heart.php file used by the Backup Migration plugin attempts to include a file based on the value of the BMI_ROOT_DIR constant, which is subject to user control. Wordfence reported the critical security flaw to BackupBliss, the development team behind the plugin, and a patch was released within hours.
WordPress has released version 6.4.2 that addresses a remote code execution (RCE) vulnerability that could be chained with another flaw to achieve RCE. The vulnerability was identified in a class that was introduced in WordPress 6.4 to improve the performance of the CMS. The vulnerability can be combined with a different object injection flaw, allowing attackers to execute PHP code on vulnerable websites. Although the flaw isn’t critical on its own, due to the need for object injection on installed and active plugins or themes, the presence of an exploitable POP chain in WordPress core significantly increases the overall risk. WordPress added a new method that prevents the vulnerable function from executing, thus preventing exploitation. Site owners and administrators are advised to update to the fixed CMS version as soon as possible.
Wordfence brought a critical security vulnerability to the attention of BackupBliss, the team responsible for developing the Backup Migration plugin, on December 6. Swiftly responding to the report, the developers released a patch within hours, unveiling the updated Backup Migration 1.3.8 plugin version on the same day. However, despite the prompt fix, recent statistics from WordPress.org indicate that nearly 50,000 websites continue to operate with a vulnerable version of the plugin, even almost a week after the release of the patch.
It is strongly recommended that website administrators take immediate action to secure their sites against potential attacks exploiting the identified vulnerability, denoted as CVE-2023-6553. This critical security flaw poses a significant risk, as unauthenticated malicious actors can exploit it remotely, potentially compromising the integrity and functionality of the affected WordPress websites.
In addition to this security concern, WordPress administrators find themselves contending with a phishing campaign specifically targeting them. The campaign aims to deceive administrators into unwittingly installing malicious plugins by employing fake WordPress security advisories. These advisories falsely reference a non-existent vulnerability identified as CVE-2023-45124, acting as bait to lure unsuspecting administrators into compromising their website security.
Notably, in the preceding week, WordPress addressed another security issue—a Property Oriented Programming (POP) chain vulnerability. This particular vulnerability had the potential to permit attackers to execute arbitrary PHP code under specific conditions. The risk was especially pronounced in multisite installations when combined with certain plugins. The timely resolution of such security concerns underscores the ongoing importance of vigilance and proactive measures in maintaining the security of WordPress websites.
Citations:
https://www.bleepingcomputer.com/news/security/50k-wordpress-sites-exposed-to-rce-attacks-by-critical-bug-in-backup-plugin/
https://www.darkreading.com/cloud-security/critical-wordpress-plugin-rce-bug-exposes-websites-takeover
https://www.securityweek.com/wordpress-6-4-2-patches-remote-code-execution-vulnerability/
https://www.bleepingcomputer.com/news/security/wordpress-fixes-pop-chain-exposing-websites-to-rce-attacks/
https://securityaffairs.com/155573/security/wordpress-6-4-2-rce.html